Cell network explanation — Thearchy Chain/Subchain structure
In a recent interview, Dr. Xiang Yu likened the INT structure to that of a Cell Phone network. Much like how cellular networks work, where the network is distributed in geographic areas called cells and each cell is connected to the network by at least 1 cell tower, the INT network will be a network of digitally separate cells which are side chains, and each side chain is connected to the greater network by at least 2 supernodes.
This is done in cell networks, in part, to manage network congestion. Each cell tower manages the connection to the greater network and other cell areas by using one defined frequency or path. This is unlike large transmitters, where there is one path to the network that can get congested, these cells add additional paths like adding lanes to a highway.
We see this issue in single chain blockchains like Bitcoin where in times of large transaction volumes, the network gets congested with transactions and a backlog begins to build.
INT’s concept is along the same theology, by creating subchain cells to manage connection to the network, where the supernodes (like the cell towers) do the transaction processing and pass batched transactions on to the greater network, transaction congestion will be secluded and managed within the subchains and not affect the main network [Fig. 1]. This will allow easy scaling by adding subchains and supernodes to manage transaction volume.
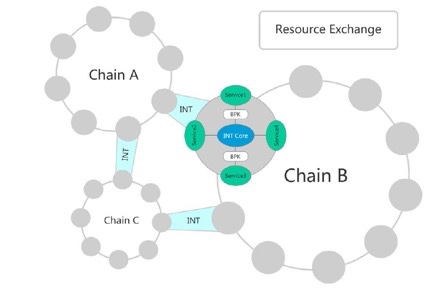
Fig. 1 INT chain structure
Zero-Knowledge proofs (zk)
Zero knowledge proofs are not easy to describe without using complex analogies or mathematics. Essentially what it does is allows you to prove that I know a secret without revealing what the secret actually is. It is used, most importantly, in identity authentication (protecting node identity, IoT device ownership, etc.), verifying transactions without knowing any details about the sender, recipient or other transaction details. It is unclear at this time how they will go about implementing this into their protocols, but they have mentioned the importance of user and data privacy in the coming IoT data revolution. Implementing ZKP is something that, to my knowledge, has yet to be successfully implemented in a smart contracting blockchain.
Double Chain Consensus Algorithm — Device Communication Protocols
The INT P2P architecture will use DHT to organize network nodes and will utilize both TCP/IP and UDP/IP as the basis of their communication protocols. This will allow IoT devices to be able to seamlessly integrate with the INT network, even in highly mobile or bad connection environments.
DHT networks are decentralized networks of distributed hash tables. These are used as lookup tables for key pairs so that nodes can efficiently retrieve values associated with a given key. This can be used to maintain a list of node addresses and public keys (miner nodes, super nodes, meta nodes), IoT devices and their associated keys as well as distributed file systems and peer to peer information sharing. This will be the keystone of the node network and IoT device information transfer.
TCP/IP and UDP/IP are both protocols used for sending data packets through the internet. TCP is the most commonly used protocol on the internet. The general structure for a transaction from device to node (once you know the IP of the node via the DHT) would be: the device sends a request for connection to the node, the node would acknowledge the request, the transaction would be sent to the node, the node would signal a verification that the data was received correctly, the device would signal a connection close, the connection would close.
This can also be done in the other direction, say by connecting your wallet to a node to download the block chain. As follows: the device sends a request for connection to the node, the node would acknowledge the request, the data would be sent to the device in packets, each numbered in order, the device would signal on each successful arrival of a packet the packet number it received, once all packets are sent and received with no errors, the device will signal a connection close and the connection will close.
TCP is about data transmission reliability but you can see that it does this at the expense of complexity and resource intensive checks on connection and data validity. This is very useful in many cases but causes issues when operating with highly mobile devices connecting to the network (phones, vehicles) and devices in bad connection environments.
UDP is a much more lightweight protocol, using the same data packet but throwing out all the error checking and back and forth communication out in favor of a simple, one time data bullet heading for the node. There is no check to see if it is listening or if it received it. It the node misses it, the device won’t resend it, it will just send the next packet and so on. This is best for things like live broadcasting and high volume (multiple transactions per minute) data readings where missed information isn’t a large impact.
The integration of both these protocols will allow all devices to communicate with the network and seamlessly switch between the protocols which best suits the purpose at the time.
In one of the latest weekly updates they also hinted at mobile ad hoc networks (MANET). MANET is a continuously self-configuring, infrastructure-less, network of mobile devices connected wirelessly. This is much more complex than the above networks where each device has a defined path to route data. In a MANET, each device must forward traffic unrelated to its own use and, therefore, act like a router for the devices that are connected to it. These networks may operate by themselves or be connected to the internet. They don’t specify their intentions with this area of development but it has some interesting applications in nullifying the impact of devices moving in and out of network connection by being connected to one another and storing the data of their peers or by creating a node network to allow nodes to distribute traffic automatically and other more complex networks of sensors that begin to act like an artificial intelligence. Implementing this will be a tremendous task.
From:https://medium.com/@graytrain/int-thearchy-subchain-architecture-and-device-communication-protocol-an-explanation-9cfeac9e75a7.
By Graytrain

最新回复